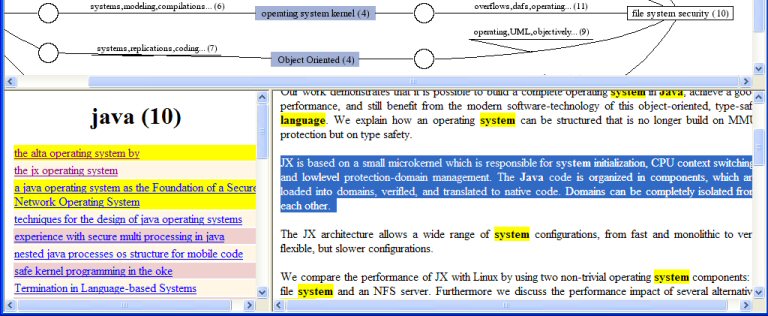
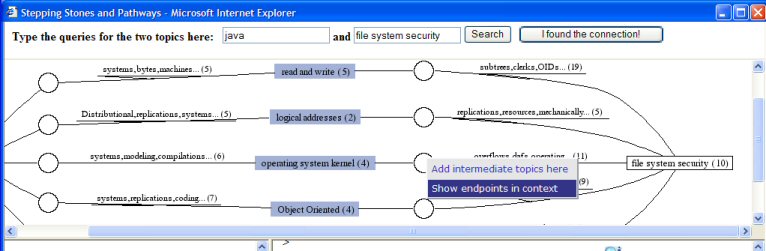
So, you would type "Java" in one box, and "file system security" in the other. You could type more words, whatever you think describes the topics. The first network of connections appears in a few seconds:
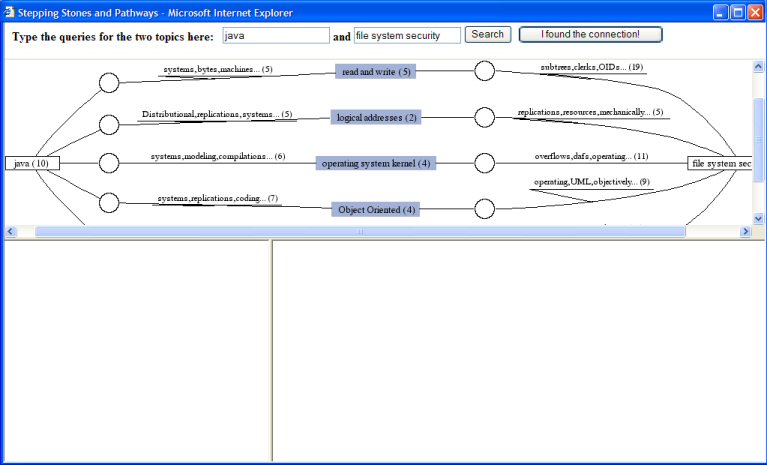
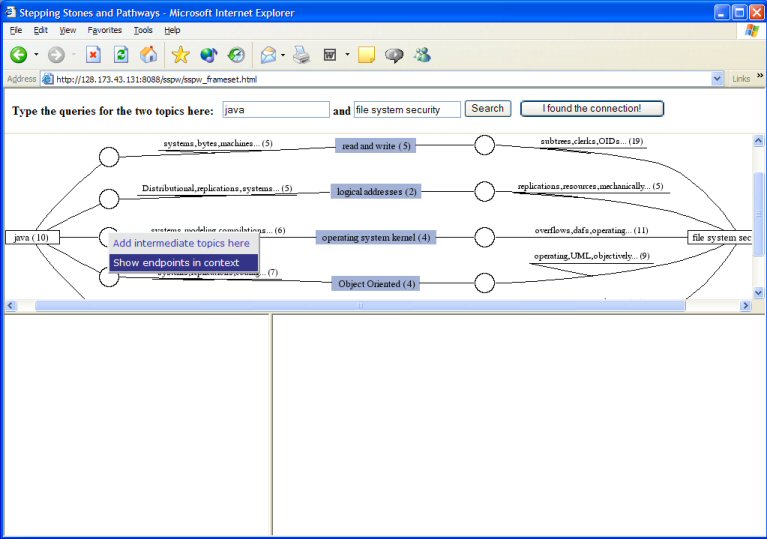
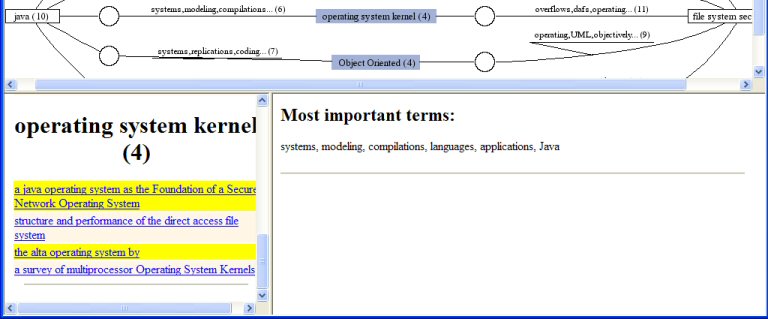
You see that there are different topics connecting "Java" and "file system security". One of them is "operating system kernel". You move the mouse to the circle on the line between "Java" and "operating system kernel", and a pop-up menu appears. You select "show endpoints in context" on the pop-up menu, to see the documents about "Java" and "operating system kernel" (the endpoints) at the same time, ordered by how each document relate to the other topic (the context).
You see some documents appear both under the topics "Java" and "operating system kernel", as they are highlighted in bright yellow (This doesn't always have to be the case; most of the time the documents in each topic are not repeated, but related by their content).
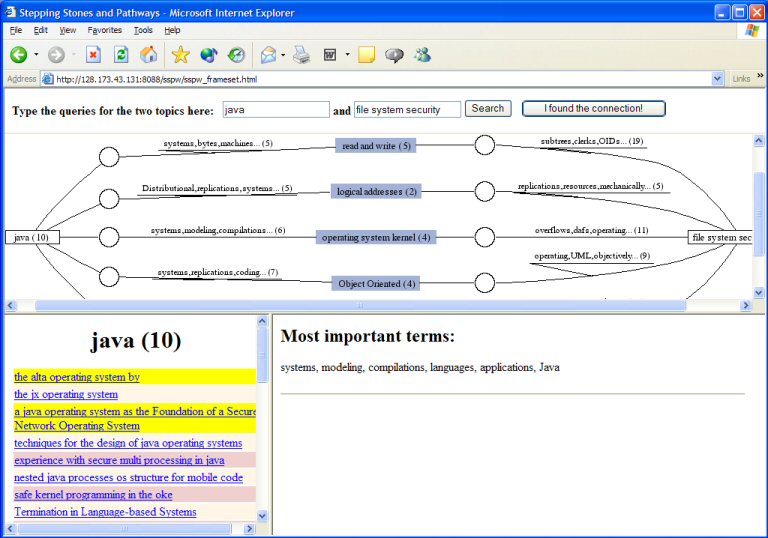
...by scrolling down on the left bottom area, you can also see the documents related to "operating system kernel":
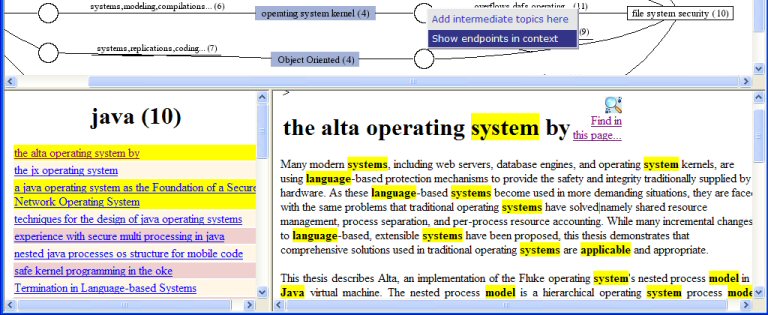
You decide to explore the document titled "the alta operating
system by". You click on the title to read it, and you find that
it talks about Alta, an OS
implemented in Java:
We also see
there are other documents about java and operating systems:
"The JX operating system", "A Java operating system as the Foundation
of a Secure Network Operating System", and others.
You go next to the circle over the line connecting "operating system kernel" and "file system security", the pop-up menu appears and you select "show endpoints in context" again, to see how these two topics are related:
... the list of documents appears:
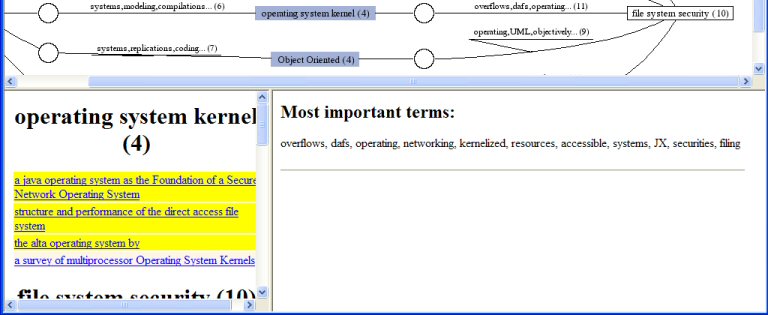
and you see that "The Alta operating system" "a java operating system as the Foundation of a Secure Network Operating System" are there, and both appear under "Operating System Kernel" and "File system security", because they are highlighted in bright yellow.
Reading "The Alta operating system" again, we find is related about file systems and Java , but not to security in file systems. Next we explore "A java operating system as the Foundation of a Secure Network Operating System".
We find the following paragraph:
[...speaking about implementation errors and buffer overflows in OS]:
"JX addresses these errors by following well-known principles, such as least-privilege and separation-of-privilege, and by using a minimal security kernel, which, for example, excludes the filesystem."We remember now we saw a paper about JX in the connection between "Java" and "Operating System Kernel". We click again over "show endpoints in context" on the connection between "Java" and "Operating System Kernel", and we click over the title "The JX Operating System". We find the following paragraphs:
"This paper describes the
architecture and performance of the JX
operating system. JX is both an operating system completely written in
Java and a runtime system for Java applications."
...and...
"JX is based on a small microkernel which is responsible for
system
initialization, CPU context switching, and lowlevel protection-domain
management. The Java code is organized in components, which are loaded
into domains, verifled, and translated to native code. Domains can be
completely isolated from each other."